Device Control Plus is a robust device management software that can be leveraged to implement effective role-based access control (RBAC) which is a cybersecurity approach designed to prevent unauthorized access by granting access permissions only to appropriate users, based on their job titles or tasks owned. As organizations scale up their employee count, regulating access permissions is one of the most crucial steps in mitigating data loss. With Device Control Plus, you can protect your valuable data by configuring extensive device and file access permissions in just a few clicks.
To effectively set up a role-based access control system, an RBAC software solution can be utilized. The main rules of RBAC security are to classify all users into various roles, provide authorization for each user depending on their role and function and lastly assign the appropriate permissions. With Device Control Plus, a complete device and file action control solution, administrators can enforce role-based access control and have it automated in three simple steps:
The primary step to enacting role-based security is to assign roles. This can be done by distinguishing between the various users within the business and their diverse functions. Typically these roles are based on the job titles that fall under major divisions such as finance, marketing, human resources, etc. With Device Control Plus, administrators can provide a name and a description for each role-based access control policy that they create. For easy categorization and tracking of these policies, you can name them by the job title they apply to, and in the description, you can elaborate on the department as well as other salient details about that role.
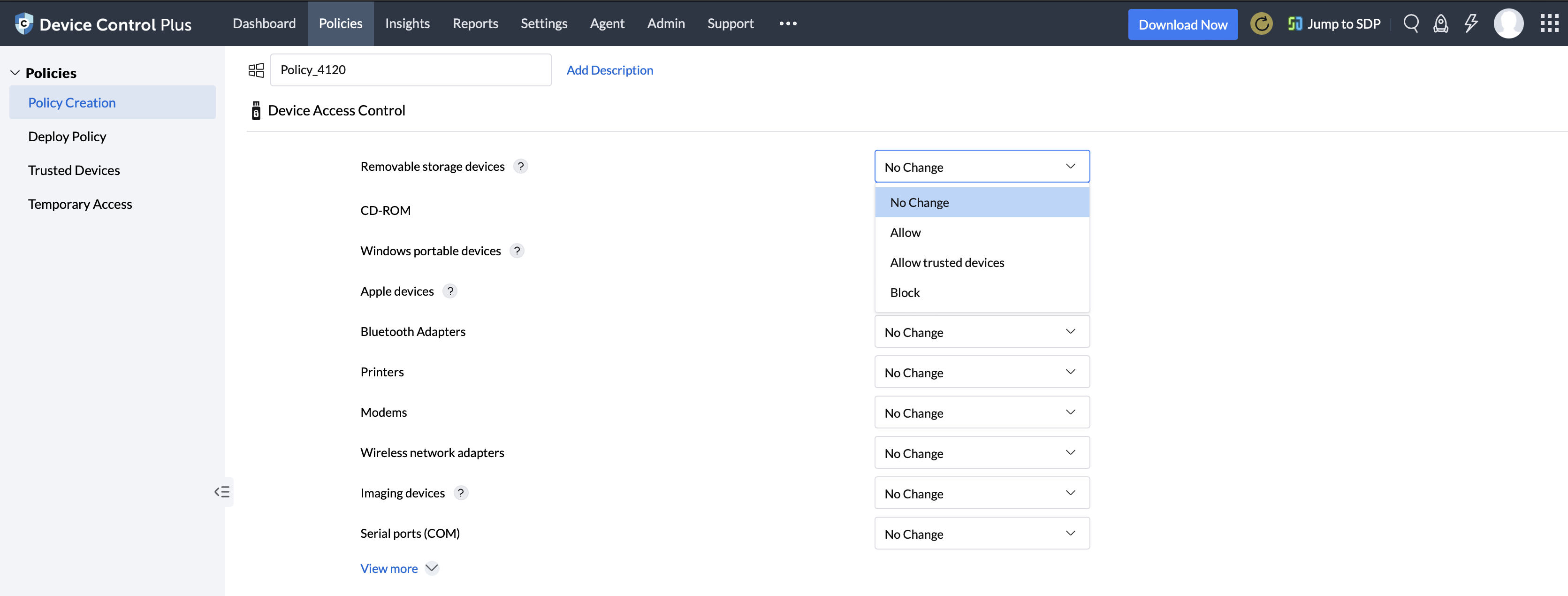
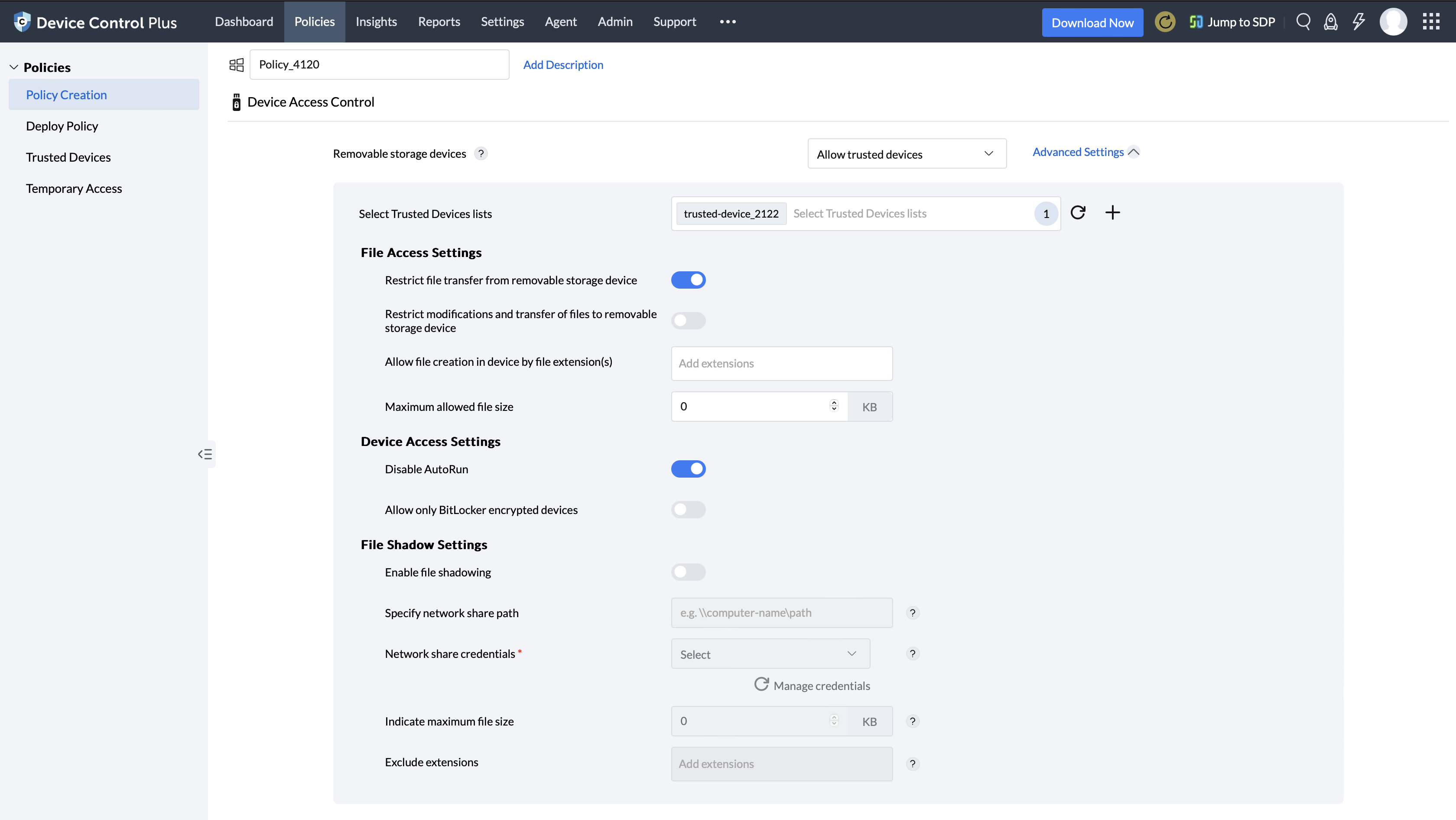
After a policy is named and its description is filled in accordance with a role, the settings can be configured. First, the devices that belong to the more prominent users who have administrative or executive roles can be added into the whitelist. These devices can be granted increased/higher mobility when it comes to accessing various information across their department. Then, for the majority of the other employees, their devices can be given read-only permissions or delegated specific rights to access only the information critical to their job requirements while access to all other data remains restricted.
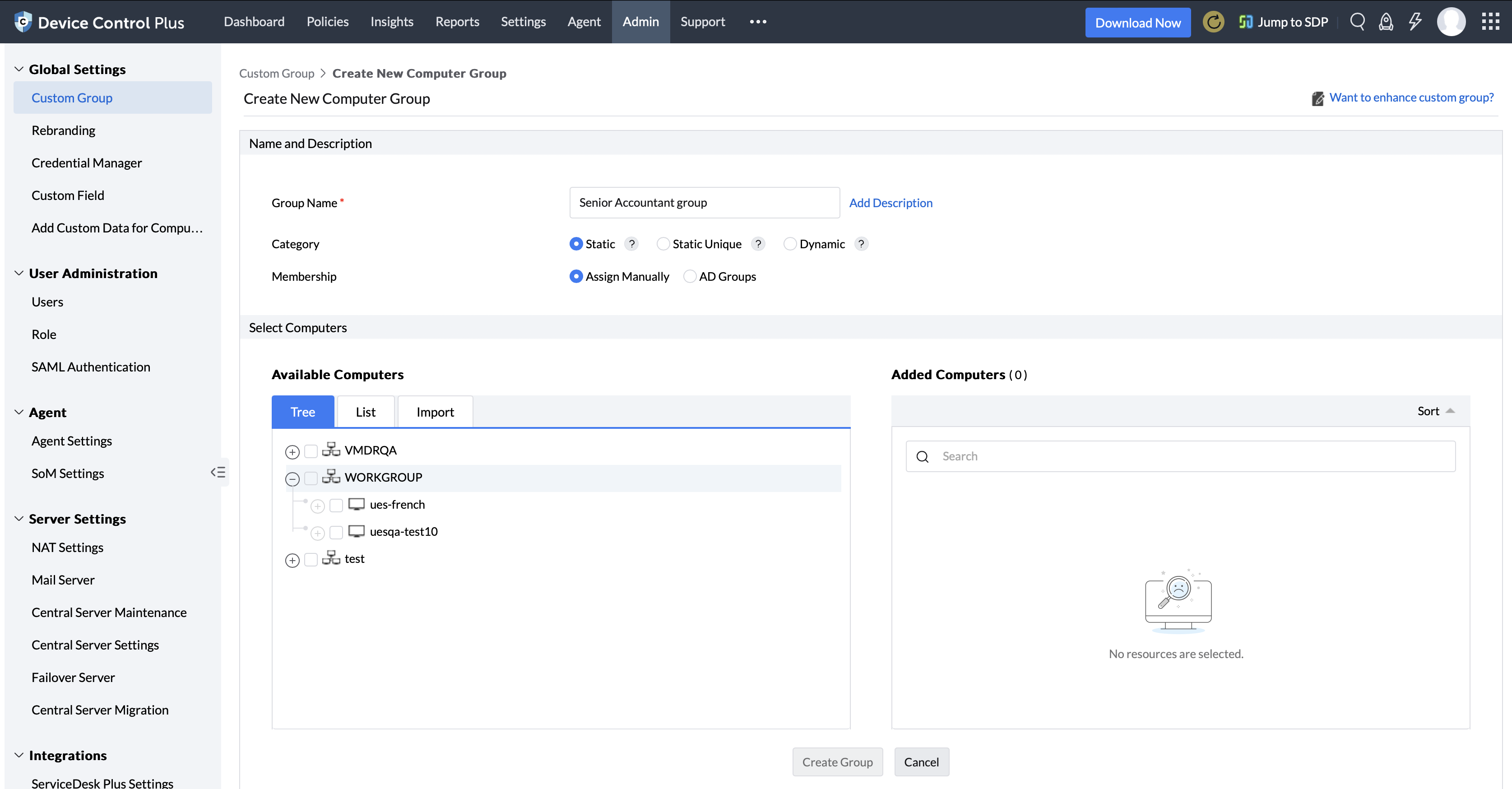
Custom groups of computers can be created based on various occupational divisions present within an organization; however, since some jobs require certain types of machines to fulfill their itinerary, custom computer groups can be formulated based on functions performed by users with a particular job title. The created policies can then be simultaneously applied to entire departments or users with a specific role by mapping them to the apposite custom groups.
For example, let's consider an organization named Zylker. To implement RBAC, Zylker's IT administrator first classifies employees based on their role, department, organizational hierarchy, or geolocation according to the organization's preference. On Device Control Plus, the administrator then creates individual access control policies for all the roles, with custom policy names and descriptions, as explained in the first step.
Having labelled Zylker's policies, next comes configuring the settings under each policy. The administrator adds devices belonging to prominent employees such as top-level executives into a whitelist, to grant elevated access control like file-copying or write permission, while restricting the same for other roles. For example, auditors or contract employees can be given read-only permissions, while their managers are granted write access, and Zylker CEO's devices are added into the whitelist for increased mobility.
The last step in implementing RBAC is to create custom groups based on Zylker's role assignment done by the administrator in the first step. For example, all computers belonging to remote workers can be added to a custom group, to which an access control policy with only read access enabled can be mapped.
Role-based access control is the technique of assigning access permissions to the users in your organization based on their roles and the tasks they perform. Role-based access control security ensures that users only have access to the information or files that are relevant to their current position or project. In organizations that have major divisions, enacting a role-based access control system is essential in mitigating data loss.
For many organizations, since they are divided into multiple departments that have their own set of dedicated employees often with their own computers, the Device Control Plus role-based access control system is the best RBAC solution to apply for optimal security. If file access permissions are based on one set of rules and universally applied throughout the organization, then the security impositions could either be too rigid and can obstruct an employee's workflow or too lenient which could result in hidden loopholes for attackers. With role-based security, administrators can achieve both optimal security and productivity by granting varying levels of permissions to users based on their role, so that while authorized users can easily access information pertaining to their department and specific function, access to all other company data remains restricted.
For both large enterprises and SMBs, Device Control Plus offers capabilities that aid admins in achieving granular control over devices and user actions. Even when there are numerous device connections occurring daily, each device will be promptly detected and can be given tailored access permissions based on the owner and the relevancy of their office-related tasks. Each user will be able to view and transfer the data they need while the rest of the organizations' data remains intact and protected from disclosure or tampering. Any data that is moved can also be traced and shadowed so that analysts can leverage the audit data to further improve their role-based access control (RBAC) policy efficacy
When it comes to air-tight cyber-hygiene, organization is key. Through delegating user permissions by following RBAC security protocols, both users and admins alike can be afforded clarity as to the functions of employees and their resource requirements which can lead to significantly improved administrative efficiency when building policies.
Grant user privileges according to individual users and their task at hand. Through role based access control, grant access to only mission-critical data and keep all other confidential information in lock down.
With the role based access control capabilities in Device Control Plus, admins can easily prepare role-based access control policy templates beforehand for the various roles in their organization. New members can be methodically attributed to a particular policy based on their job title. If needed, the policies can be quickly fine tuned to meet the specific requirements of the individual.
By implementing RBAC security, effectively satisfy the requirements of all members of the organization by granting specific user permissions. In parallel, adhere to all the industry standards and regulations for privacy.
Create custom groups of computers based on departments, job titles, etc. In order to protect data effectively, users should only have access to information that is necessary for their work role. To establish more stringent control, custom groups should be further divided into tiers. For example, within the IT department of a company, a group can be created for computers belonging to trainees and another group for computers designated for mentors and supervisors.
Often organizations encourage collaboration between different divisions, which leads to the formation of cross-functional project teams. Though many of these employees have different job titles, they may all require access to the same pool of information for certain tasks. In such cases, the devices owned by the members involved in this event can be whitelisted, and you can associate the policy created specifically for their device with a custom group that consists of machines operated by them as well.
Since there is always a constant influx of employees whether they're new or from other parts of the organization, their devices should promptly be categorized as trusted or blocked, and their computers should be inserted into a custom group. This best practice also applies if existing users obtain new equipment. This proactive approach ensures that device and file control policies are enforced right from a user's introduction and through the rest of their career in the company, so that their activities always remain monitored, and there's no opportunity for data loss.
Prevent file based attacks with an effective role based access control software, download a 30 day, free trial of Device Control Plus!