Firewall change management should be used before making changes to firewall or IDPS rules that affect users. A concrete firewall change management and firewall configuration monitoring process helps ensure complete cohesion in managing changes in your network.
Firewall Analyzer fetches the firewall configuration using CLI or API from your firewall devices and enables you to keep an eye on the changes being made to the network security infrastructure. Administrators may commit an unintentional error or carry out an improper change while acting on a firewall configuration change request giving room for breaches. This feature ensures that all the configurations and subsequent changes made in the Firewall device are captured periodically and stored in the database. Firewall Analyzer's configuration change management reports precisely helps find out 'who' made 'what' changes, 'when' and 'why' to the firewall configuration.
The following are the reports generated by this firewall configuration analysis tool.
The Firewall Change Management reports can be scheduled and distributed via Email and can be exported to different formats. Not only that, you can also filter the firewall configuration change management report for known and recurring changes which clutters the report. Firewall Analyzer will exclude the lines in the report, matching the specified criteria (Exclude Criteria) for all or selected devices.
Firewall Analyzer (Firewall Change Management Software) generates alerts for the Firewall device configuration changes in real-time and it notifies via Email, SMS. Hence any change made to the firewall configuration is notified to the security admin and this beneficial in effective firewall change monitoring.
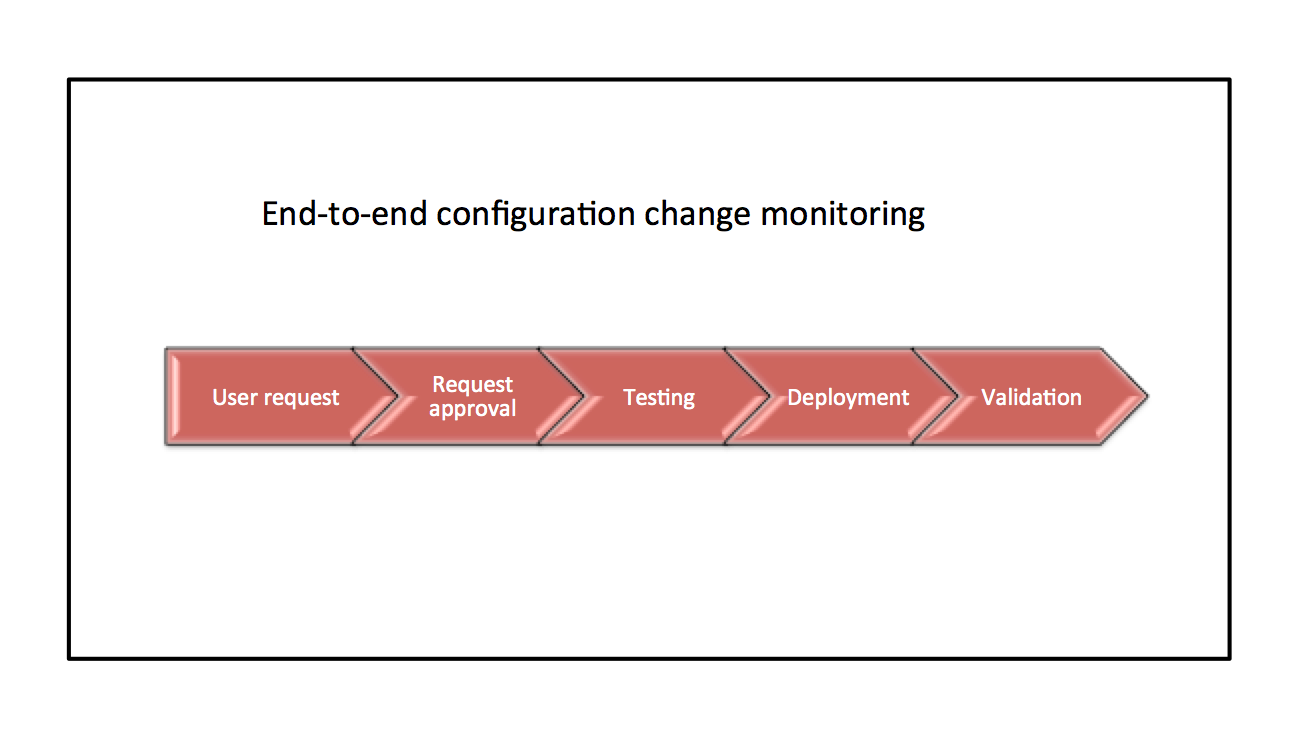
In any organization, frequent firewall changes are a necessity when it comes to network security. Putting into place a streamlined firewall change management policy template reduces management time and also the chance of introducing new security or compliance issues with each change. A typical firewall change management process would include the following steps:
To get a complete list of supported vendors, click here. Firewall Analyzer also uses the firewall configuration to generate firewall policy management, security audit and compliance standards reports.
Featured links
Get a slew of security and traffic reports to asses the network security posture. Analyze the reports and take measures to prevent future security incidents. Monitor the Internet usage of enterprise users.
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.